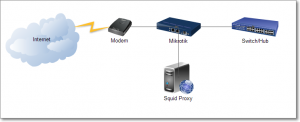
Mikrotik routerboard has a built-in proxy in it, but it has main constraint : very limited storage capacity. Therefore, most network administrators whom using mikrotik will use an external proxy to overcome this constraint. Here you can found an easy ways to implementing external proxy server for Mikrotik.
Squid is the most widely used proxy daemon for linux (including its derivative such as lusca). Some several advantages in the implementation of external proxy are :
- Easy to adjust the configuration to suite your needs
- The use of access control lists (ACLs) that can be used for specific purposes
- Squid (especially version 2.7) can be “armed” with a url redirector. In some condition, url redirector can be used to force squid to cache dynamic content (such as Youtube videos).
- Greater storage capacity as the general computer or server use the harddisk as data storage.
In this post, I’ll describe how to integrate external proxy with mikrotik using 2 methods : using NAT or using mangle.
Annotation :
- Mikrotik to proxy IP address : 192.168.90.1
- Proxy to Mikrotik IP address : 192.168.90.2
- Clients IP address : 192.168.1.0/24
/ip firewall address-list add address=192.168.90.0/24 list=ip-proxy /ip firewall nat add action=dst-nat chain=dstnat comment="transparent proxy" dst-port=80 protocol=tcp src-address-list=!ip-proxy to-addresses=192.168.90.2 to-ports=3128
Explanation :
First, we define IP address class for proxy server.
/ip firewall address-list
add address=192.168.90.0/24 list=ip-proxy
Then add new rule on NAT to forward http request to external proxy.
/ip firewall nat
add action=dst-nat chain=dstnat comment=”transparent proxy” dst-port=80 protocol=tcp src-address-list=!ip-proxy to-addresses=192.168.90.2 to-ports=3128
Second method : Using built-in mangle
/ip route add check-gateway=ping distance=1 gateway=192.168.90.2 routing-mark=to-ext-proxy /ip firewall mangle add action=mark-routing chain=prerouting comment="mark routing to proxy" dst-port=80 new-routing-mark=to-ext-proxy protocol=tcp src-address=192.168.1.0/24
Another method to forward http requests from clients is using mangle by adding new route. This method will work if external proxy able to act as gateway.
Explanation :
First, add route to external proxy.
/ip route
add check-gateway=ping distance=1 gateway=192.168.90.2 routing-mark=to-ext-proxy
Then, mark http requests from all clients to use route to external proxy.
/ip firewall mangle
add action=mark-routing chain=prerouting comment=”mark routing to proxy” dst-port=80 new-routing-mark=to-ext-proxy protocol=tcp src-address=192.168.1.0/24
Proxy server requirements :
You may need to configure some options in order to make it works for both methods such as enabling IPv4 forwarding (by editing systcl.conf) and allowing access to port 3128 in iptables. Add the following lines into the file /etc/rc.local then save :
route add default gateway 192.168.90.1 iptables -A PREROUTING -t nat -j REDIRECT -p tcp -s 192.168.1.0/24 -d 0/0 --dport 80 --to-ports 3128 iptables -A INPUT -p tcp -s 0.0.0.0/0 -d 192.168.90.2 -m state --state NEW,ESTABLISHED -j ACCEPT iptables -A OUTPUT -p tcp -s 192.168.90.2 --sport 3128 -d 0.0.0.0/0 -m state --state ESTABLISHED -j ACCEPT

Mr. Fazar
Thanks for your support but my situation is different that My ISP Put me behind proxy server
with no gateway he only give me the proxy server info like this :
My proxy server ip is : 172.30.7.211
My Proxy server Port : 808
When I put them is my browser the internet is working so how to add this info in mikrotik to
deliver internet to my clients ??
If the proxy server also acts as gateway, you can use mangle then route the internet traffic to it. but if its run as standalone proxy that only accept connection on defined port, the only way to do it is using NAT. The problem is, you can proxify all HTTP (port 80) traffic, but not HTTPS (port 443) because its encrypted.
Bang Fajar minta tolong dong, masih belum bisa proxy saya.
Saya berencana menggunakan mode transparent proxy dengan ubuntu server dan mikrotik. Topologi nya
Inet — Mikrotik —- Client
|
|
proxy
Mikrotik to client 192.168.3.1
Mikrotik to proxy 192.168.2.1
Proxy to Mikrotik 192.168.2.2
saat browser client saya paksa add proxy ke 192.168.2.2 koneksi bisa dilakukan, tapi waktu dibuat transparent connection timed out.
konfigurasi squid.conf:
#acl manager proto cache_object
#acl localhost src 127.0.0.1/32 ::1
#acl to_localhost dst 127.0.0.0/8 0.0.0.0/32 ::1
#acl localnet src 10.0.0.0/8 # RFC1918 possible internal network
#acl localnet src 172.16.0.0/12 # RFC1918 possible internal network
acl localnet src 192.168.0.0/16 # RFC1918 possible internal network
#acl localnet src fc00::/7 # RFC 4193 local private network range
#acl localnet src fe80::/10 # RFC 4291 link-local (directly plugged) mac$
acl SSL_ports port 443
acl Safe_ports port 80 # http
acl Safe_ports port 21 # ftp
acl Safe_ports port 443 # https
acl Safe_ports port 70 # gopher
acl Safe_ports port 210 # wais
acl Safe_ports port 1025-65535 # unregistered ports
acl Safe_ports port 280 # http-mgmt
acl Safe_ports port 488 # gss-http
acl Safe_ports port 591 # filemaker
acl Safe_ports port 777 # multiling http
acl CONNECT method CONNECT
http_access allow manager localhost
http_access deny manager
http_access deny !Safe_ports
http_access deny CONNECT !SSL_ports
http_access allow localnet
http_access allow localhost
http_access deny all
http_port 3128
hierarchy_stoplist cgi-bin ?
coredump_dir /var/spool/squid
refresh_pattern ^ftp: 1440 20% 10080
refresh_pattern ^gopher: 1440 0% 1440
refresh_pattern -i (/cgi-bin/|\?) 0 0% 0
refresh_pattern . 0 20% 4320
konfigurasi /etc/rc.local:
route add default gateway 192.168.2.1
iptables -A PREROUTING -t nat -j REDIRECT -p tcp -s 192.168.3.0/24 -d 0/0 –dport 80 –to-ports 3128
iptables -A INPUT -p tcp -s 0.0.0.0/0 -d 192.168.2.2 -m state –state NEW,ESTABLISHED -j ACCEPT
iptables -A OUTPUT -p tcp -s 192.168.2.2 –sport 3128 -d 0.0.0.0/0 -m state –state ESTABLISHED -j ACCEPT
http port sudah saya ubah ubah dg skenario
1. pakai plain http port 3128
2. ada dua http port:
http_port 3128
http_port 8080 transparent
tapi kedua cara itu sama aja, client kalo dipaksa pake proxy tersebut mau koneksi, tapi kalo pake transparent tidak bisa konek
realy hope to your help for my study assignments, big thanks
revisi: topologi nya bukan seperti itu bang, inet >> mikrotik nyabang 2 >> 1. proxy, 2. clients
bagusnya sih pake mikrotik yg sejajar proxy. kalo yg saya tangkep, masalahnya kalo di set proxy manual (di browser) bisa jalan. tapi kalo di transparent kan, nggak bisa jalan. gitu ya? jika demikian, silakan ricek IP > Firewall > NAT apakah port 80 klien sudah di belokkan ke proxy. di sisi proxy, periksa kembali apakah IP forwarding nya sudah di enable (file /etc/sysctl.conf cari baris net.ipv4.ip_forward. nilainya harus net.ipv4.ip_forward = 1).
iya bang, kalo diset proxy manual bisa jalan log nya, tapi kalo pake transparent gak jalan.
firewall nat sudah dibelokkan bang dari port 80 client ke 192.168.2.2:3180
IP forwarding di proxy sudah di enable jg bang
hasil masih tetap sama,
saya bingungnya kan di mikrotik sudah dibelokkan dari port 80 ke 3180 tapi kenapa di /etc/rc.local masih dibuat demikian jg bang ya? suwun
rules iptable di buat agar klien yg langsung menjadikan proxy sebagai gateway juga dapat mengakses squid secara otomatis. oh iya.. ini squid versi berapa? kalo versi 3.x coba ganti transparent jadi intercept (http_port 3128 intercept).
Mantaps sudah bisa bang, BIGGTHANKS.
sudah saya ganti intercept dan saat client dibuat transparent(tidak disetting di browser) hasilnya log nya jalan.
Satu lagi bang,ketika client access http log di squidnya jalan, tapi ketika client access https seperti facebook.com, log di squid tidak terlog.
apa itu karena cuma redirect dari port 80 aja, solusinya gimana bang?
yup, cuman port 80/HTTP aja yang di proxy. untuk port 443/HTTPS harus menggunakan SSL bump. coba google deh.. :)
Mr. Fazar
This is a great site but I need your help to receive internet to mikrotik from a proxy server
As our ISP give us internet Through proxy server.
I means that:-
Internet — Proxy Server — Mikrotik — Clients
Can you please help…
Did you mean you want to give internet access to your clients through mikrotik? If yes (I’m assuming proxy server also running as internet gateway), then you can add route to proxy server and set NAT so your clients can access internet properly. eg. proxy server IP: 192.168.0.1 – out interface ether1-WAN – client IP 192.168.1.0/24.
/ip route
add comment="Route to Proxy" distance=1 gateway=192.168.0.1
/ip firewall nat
add action=masquerade chain=srcnat comment="NAT to Proxy" out-interface=\
ether1-WAN
Ive googling so much and find this article most easy-understanding and desirable to be tried. Could I get some advices regarding to squid config especially squid.conf, I have trouble on that, thanks
squid will work even using default squid.conf, you also can fine-tune it to suite your needs. i have some articles regarding this topic, you can search it in this blog – mostly it cover (outdated) squid 2.7 configurations.
Great article!
There is a demand for a better blacklist. And with few alternatives available, we intend to fill that gap.
It would be our pleasure to serve you,
Signed,
Benjamin E. Nichols
http://www.squidblacklist.org
i tried last step but didn’t worked for me i think add route should solve my problem can u correct me if route is the solve with example route command for redirecting incoming port 80 request
sir im usind squid alternative proxy server
i want to raoute all proxy:3128 to incoming request assume my proxy server should act as gateway im not using mikrotek board im using simple wireless router and i want my machine be able to use net using proxy if as gateway and the ip lease which i allowed in proxy server e.g 192.168.1.2 netmask 255.255.255.0 gateway which is proxy ip 192.168.1.16
i can use my proxy using web proxy setting but i wanted to use it wihout web setthing means directly i get access to web using proxy as gateway
right now im doing it as test or educational purpose proxy is virtual and net i want in physical machine plz advice
I am assuming your proxy act as gateway + dhcp server, using two interface (eg. eth0 = internet, eth1 = lan), and able to connect to internet properly . in order to make clients browse internet through proxy without setting up proxy manually on browser, you need to setup squid with transparent / intercept configuration directive as described here :
http://www.squid-cache.org/Doc/config/http_port/
and finally, redirect all http access to proxy using iptables. you can read detailed how-to here :
http://www.tldp.org/HOWTO/TransparentProxy-6.html
it is not necessary to set static route, since it only useful for proxy box with single network interface.
Yes, Now all traffic going to squid.
But the only one ip add 192.168.90.1.
I need all client original ip address.
how it is possible.Please help
Thanks in advance.
hello shaon. sorry for my late response.
with current iptables rules, all incoming connection in eth1 with dest. port 80 (http) should be redirected to squid. re-check your squid configuration (squid.conf), ensure your have configuration like this:
http_port 3128 intercept
next thing to do is, use your squid box IP address (192.168.90.2) as your clients gateway. use google dns as your clients primary/secondary DNS.
if you installing dns resolver in your squid box (eg. pdnsd, bind, dnsmasq, etc), you can use 192.168.90.2 as clients primary dns server. hope that help. :)
using
rhel 6.4
squid 3.1
I am assuming you are using 2 interface, right? (eth0 and eth1). This tutorial only use single interface and using mikrotik router as gateway. In short, this tutorial wouldn’t meet your requirements. :)
flush your iptables rules and use this rules:
iptables -t nat -A PREROUTING -i eth1 -p tcp –dport 80 -j REDIRECT –to-port 3128
iptables -t nat -A POSTROUTING -o eth0 -j MASQUERADE
and don’t forget to set IPv4 forwarding in sysctl. good luck! :)
Boss, why Not working for me, After configure with my working transparent proxy ,i even unable to ping google .
[root@nat ~]# route
Kernel IP routing table
Destination Gateway Genmask Flags Metric Ref Use Iface
182.160.-.- * 255.255.255.240 U 0 0 0 eth0
192.168.90.0 * 255.255.255.0 U 0 0 0 eth1
link-local * 255.255.0.0 U 1002 0 0 eth0
link-local * 255.255.0.0 U 1003 0 0 eth1
default 192.168.90.1 0.0.0.0 UG 0 0 0 eth1
default 182.160.-.- 0.0.0.0 UG 0 0 0 eth0
——————————————-
eth1:192.168.90.2
gat:eth0 wan ip
—————————————–
[root@nat ~]# iptables -L -n
Chain INPUT (policy ACCEPT)
target prot opt source destination
ACCEPT tcp — 0.0.0.0/0 0.0.0.0/0 tcp dpt:3128
ACCEPT tcp — 0.0.0.0/0 192.168.90.2 state NEW,ESTABLISHED
Chain FORWARD (policy ACCEPT)
target prot opt source destination
ACCEPT all — 0.0.0.0/0 0.0.0.0/0
ACCEPT all — 0.0.0.0/0 0.0.0.0/0
Chain OUTPUT (policy ACCEPT)
target prot opt source destination
ACCEPT tcp — 192.168.90.2 0.0.0.0/0 tcp spt:3128 state ESTABLISHED