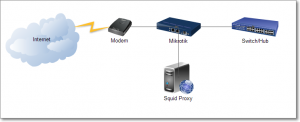
Mikrotik routerboard has a built-in proxy in it, but it has main constraint : very limited storage capacity. Therefore, most network administrators whom using mikrotik will use an external proxy to overcome this constraint. Here you can found an easy ways to implementing external proxy server for Mikrotik.
Squid is the most widely used proxy daemon for linux (including its derivative such as lusca). Some several advantages in the implementation of external proxy are :
- Easy to adjust the configuration to suite your needs
- The use of access control lists (ACLs) that can be used for specific purposes
- Squid (especially version 2.7) can be “armed” with a url redirector. In some condition, url redirector can be used to force squid to cache dynamic content (such as Youtube videos).
- Greater storage capacity as the general computer or server use the harddisk as data storage.
In this post, I’ll describe how to integrate external proxy with mikrotik using 2 methods : using NAT or using mangle.
Annotation :
- Mikrotik to proxy IP address : 192.168.90.1
- Proxy to Mikrotik IP address : 192.168.90.2
- Clients IP address : 192.168.1.0/24
/ip firewall address-list add address=192.168.90.0/24 list=ip-proxy /ip firewall nat add action=dst-nat chain=dstnat comment="transparent proxy" dst-port=80 protocol=tcp src-address-list=!ip-proxy to-addresses=192.168.90.2 to-ports=3128
Explanation :
First, we define IP address class for proxy server.
/ip firewall address-list
add address=192.168.90.0/24 list=ip-proxy
Then add new rule on NAT to forward http request to external proxy.
/ip firewall nat
add action=dst-nat chain=dstnat comment=”transparent proxy” dst-port=80 protocol=tcp src-address-list=!ip-proxy to-addresses=192.168.90.2 to-ports=3128
Second method : Using built-in mangle
/ip route add check-gateway=ping distance=1 gateway=192.168.90.2 routing-mark=to-ext-proxy /ip firewall mangle add action=mark-routing chain=prerouting comment="mark routing to proxy" dst-port=80 new-routing-mark=to-ext-proxy protocol=tcp src-address=192.168.1.0/24
Another method to forward http requests from clients is using mangle by adding new route. This method will work if external proxy able to act as gateway.
Explanation :
First, add route to external proxy.
/ip route
add check-gateway=ping distance=1 gateway=192.168.90.2 routing-mark=to-ext-proxy
Then, mark http requests from all clients to use route to external proxy.
/ip firewall mangle
add action=mark-routing chain=prerouting comment=”mark routing to proxy” dst-port=80 new-routing-mark=to-ext-proxy protocol=tcp src-address=192.168.1.0/24
Proxy server requirements :
You may need to configure some options in order to make it works for both methods such as enabling IPv4 forwarding (by editing systcl.conf) and allowing access to port 3128 in iptables. Add the following lines into the file /etc/rc.local then save :
route add default gateway 192.168.90.1 iptables -A PREROUTING -t nat -j REDIRECT -p tcp -s 192.168.1.0/24 -d 0/0 --dport 80 --to-ports 3128 iptables -A INPUT -p tcp -s 0.0.0.0/0 -d 192.168.90.2 -m state --state NEW,ESTABLISHED -j ACCEPT iptables -A OUTPUT -p tcp -s 192.168.90.2 --sport 3128 -d 0.0.0.0/0 -m state --state ESTABLISHED -j ACCEPT

By this configuration , is it possible to see -original source client ip
from squid?
Thanx in advance
use mangle instead of NAT, so your external proxy will act as gateway for HTTP stuff. good luck :)
untuk IPfire dengan single interface apakah juga harus menggunakan iptables tambahan seperti yang diatas ya om di /etc/rc.local ???
========
route add default gateway 192.168.90.1
iptables -A PREROUTING -t nat -j REDIRECT -p tcp -s 192.168.1.0/24 -d 0/0 –dport 80 –to-ports 3128
iptables -A INPUT -p tcp -s 0.0.0.0/0 -d 192.168.90.2 -m state –state NEW,ESTABLISHED -j ACCEPT
iptables -A OUTPUT -p tcp -s 192.168.90.2 –sport 3128 -d 0.0.0.0/0 -m state –state ESTABLISHED -j ACCEPT
========
nggak perlu mas.. IPFire udah generate rules iptables untuk transparent proxy jika di web interface di setting transparent proxy enabled. :)
NAT di atas di coba untuk lan bisa mas.. tp untuk hotspot dgn login nggak nyangkut.
solusinya NAT untuk hotspot gimana mas?
kalo pake nat nggak bisa, coba pake routing.
bagi yang ingin settingan terbaru proxy dengan cache youtube 1hit full (no-range) dan mikrotik bisa add MSN saya : spider84_gun@live.com
atau FB saya http://www.facebook.com/mikrotik.medan
mas Fazar mo nanya nih..
Proxy server requirements :
You may need to configure some options in order to make it works for both methods such as enabling IPv4 forwarding (by editing systcl.conf) and allowing access to port 3128 in iptables. Add the following lines into the file /etc/rc.local then save : <= di ipfire kok gak ada ya ? apa saya yang salah liat atau ..
1. ipv4 forwarding udah di aktifkan secara default di sysctl.conf, jadi di ipfire ndak perlu di utak atik lagi. :)
2. ngedit tc.local tujuannya agar squid otomatis squid start pas pc nyala kan? silakan akses web interface > networking > kasih ceklist aja di enable on green (LAN), kemudian klik save & reload.
terima kasih mas, tutorialnya bagus banget, yang jadi pertanyaan saya untuk rule redirect proxy yang benar yang diberi tanda pentung ip proxy external diletakkan di scr address atau dst address. krn dari beberapa informasi yg saya dapatkan dari google ada yg meletakkan di scr address dan yang rule dari mas diletakkan di scr address. saya sudah coba keduanya tetap proxy external bisa berjalan. jadi diletakkan di mana yang benarnya ip proxy yang diberikan tanda pentung. terima kasih….
tanda pentung > !
hehehe.. tanda seru berarti “bukan dari” jadi src-address-list=!ip-proxy maksudnya sumber request bukan berasal dari IP proxy yg ditentukan di address list. perlu diperhatikan adalah src (source = asal/sumber) sedangkan dst (destination = tujuan). sehingga dalam kasus ini menurut ane src adalah yg pas.
Lapor Gan, BERHASIL …..
Terima kasih Tutornya, akhirnya PC jadul ane jadi bisa kepake buat IPFire, Untuk selanjut nya ane mau coba yg addon Lusca nya, Tks, More Power Gan ….
Mau tanya Mas, saya menggunakan squid tuk eksternal proxy nya dan buat mantau aktivitas usernya, cuma kita kesulitan mantau aktivitas usernya karena ip yang keluar dari mikrotik cuma 1 ip, kita maunya tiap ip user terpantau di mikrotik..
Squid berada di atas mikrotik dan mikrotik menggunakan hotspot..
gunakan squid dengan dukungan tproxy. squid 3.1 keatas udah support tproxy. silakan googling cara konfigurasinya di google. :)
mas, sy udh coba ini, cuma ko koneksinya jadi lelet ya? apa ngaruh di performa server?
coba pake yg NAT mas. :)
Hi,
Thanks for this interesting article.
I look for mikrotik router too. But my intension is, to send the whole traffic to an international proxy server to use those ip-range. Will this work with the mikrotik router too?
Joerg
did you mean route all http traffic to use international/open proxy?
yes, it work with mikrotik routerboard too. you can use nat method, by changing its to-address and to-port to meet your preferences.